Because no identity-based policy allows the kms:decrypt action – Identity-based policies in AWS provide fine-grained control over access to resources. However, they do not allow the kms:decrypt action, which can lead to confusion and security concerns. This article explores the reasons behind this limitation and discusses alternative methods for controlling access to the kms:decrypt action.
Identity-based policies are a powerful tool for managing access to AWS resources. They allow you to grant permissions based on the identity of the user, such as their user ID, group membership, or role. However, there are some actions that cannot be granted using identity-based policies, including the kms:decrypt action.
Identity-Based Policies and kms:decrypt Action: Because No Identity-based Policy Allows The Kms:decrypt Action
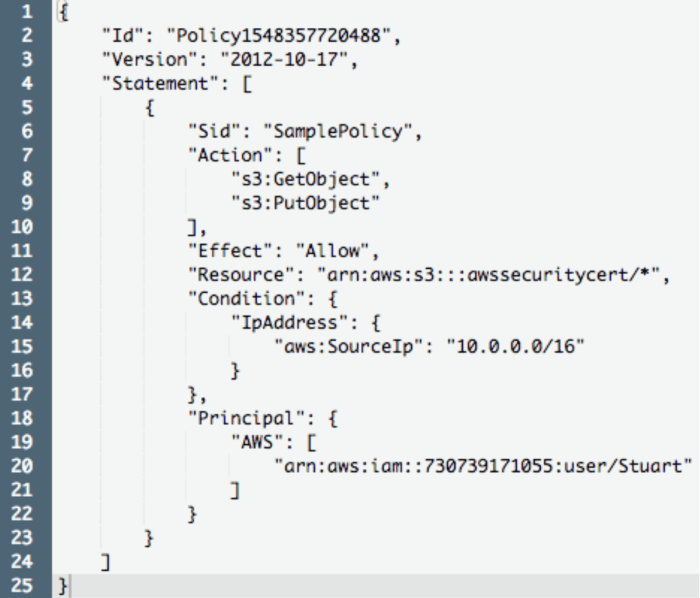
Identity-based policies (IBPs) in AWS allow you to grant permissions to AWS resources based on the identity of the principal making the request. The kms:decrypt action allows you to decrypt data that has been encrypted using a KMS key.
IBPs do not allow the kms:decrypt action because it would allow any user with the kms:decrypt permission to decrypt any data encrypted with a KMS key. This would be a security risk, as it would allow users to access data that they should not be able to access.
Alternative Methods for Controlling Access to kms:decrypt
- Resource-based policies: Resource-based policies allow you to grant permissions to AWS resources based on the resource itself. You can use resource-based policies to grant the kms:decrypt permission to specific users or groups for specific KMS keys.
- IAM roles: IAM roles allow you to grant permissions to AWS resources based on the role that the principal is assuming. You can use IAM roles to grant the kms:decrypt permission to specific users or groups for specific KMS keys.
- KMS grants: KMS grants allow you to grant permissions to KMS keys to specific users or groups. You can use KMS grants to grant the kms:decrypt permission to specific users or groups for specific KMS keys.
Best Practices for Managing Access to kms:decrypt, Because no identity-based policy allows the kms:decrypt action
- Use the principle of least privilege: Only grant the kms:decrypt permission to users or groups who need it to perform their job duties.
- Separate duties: Do not grant the kms:decrypt permission to users or groups who also have the ability to create or manage KMS keys.
- Monitor access to kms:decrypt: Regularly review the CloudTrail logs to identify any suspicious activity related to the kms:decrypt action.
Troubleshooting Common Issues Related to kms:decrypt Access
- Access denied: If a user or group is denied access to the kms:decrypt action, verify that the user or group has the appropriate permissions. Also, verify that the KMS key used to encrypt the data is accessible to the user or group.
- Decryption failed: If a user or group is unable to decrypt data, verify that the KMS key used to encrypt the data is accessible to the user or group. Also, verify that the user or group has the appropriate permissions to decrypt the data.
Case Studies and Examples of kms:decrypt Access Management
Many organizations have successfully managed access to the kms:decrypt action. For example, one organization used resource-based policies to grant the kms:decrypt permission to a specific group of users for a specific KMS key. This allowed the users to decrypt data that was encrypted with the KMS key, but they could not create or manage the KMS key.
Questions and Answers
Why can’t identity-based policies be used to grant the kms:decrypt action?
Identity-based policies are designed to control access to resources based on the identity of the user. The kms:decrypt action, however, requires access to a specific key, which is not an identity. Therefore, identity-based policies cannot be used to grant the kms:decrypt action.
What are some alternative methods for controlling access to the kms:decrypt action?
There are several alternative methods for controlling access to the kms:decrypt action, including:
- Key policies: Key policies allow you to grant permissions to decrypt a key based on the identity of the user or the role that they are assuming.
- IAM roles: IAM roles allow you to grant permissions to decrypt a key to a specific role. This can be useful for granting access to keys to applications or services that are running on EC2 instances or Lambda functions.
- Resource-based policies: Resource-based policies allow you to grant permissions to decrypt a key based on the resource that is being decrypted. This can be useful for granting access to keys to specific resources, such as S3 buckets or DynamoDB tables.